Cisco express forwarding (CEF) - contributes to the vital performance of modern networks.
CEF switching is a high-performance, Layer 3 IP switching technology developed by Cisco Systems. It serves as a forwarding mechanism for routing packets through network devices, such as routers and multilayer switches. CEF enables efficient packet forwarding by employing advanced data structures and algorithms to build and maintain a Forwarding Information Base (FIB) and an Adjacency table.
How CEF Switching Works
Unlike traditional routing methods that rely on route lookup for each packet, CEF creates a precomputed Forwarding Information Base (FIB) table during initialization. The FIB contains the necessary information to forward packets based on their destination IP addresses. This precomputation eliminates the need for per-packet route lookups, resulting in significantly improved forwarding performance.
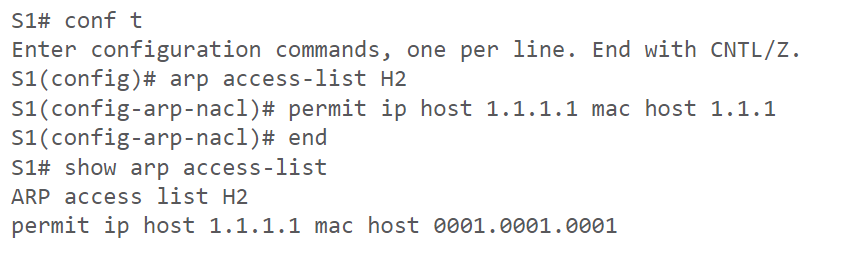
The FIB contains next-hop information, including Layer 2 (MAC) addresses, obtained through the Adjacency table. The Adjacency table stores Layer 2 information about directly connected neighbours, such as MAC addresses or ATM addresses. CEF populates the Adjacency table dynamically, reducing the need for Address Resolution Protocol (ARP) requests for each packet.
Benefits of CEF Switching
Enhanced Performance: By building and maintaining a precomputed FIB table, CEF eliminates per-packet route lookups, leading to faster packet forwarding. This acceleration improves overall network performance, reduces latency, and enhances the user experience.
Load Balancing: CEF supports multiple load-balancing algorithms, such as per-destination or per-packet load balancing. These mechanisms distribute traffic across available paths, maximizing network utilization and preventing congestion on specific links.
Scalability: CEF's efficient data structures and algorithms allow networks to handle high traffic volumes and scale seamlessly. Its ability to handle millions of routes with minimal impact on performance makes it suitable for large enterprise networks and service provider environments.
Traffic Engineering: CEF provides granular control over traffic flow by allowing administrators to manipulate the forwarding decisions. Policy-based routing, route maps, and access control lists (ACLs) can be used to direct traffic based on specific criteria, optimizing network resources and enabling traffic engineering.
Fault Tolerance: CEF enables fast convergence and minimizes network downtime in the event of link failures or network topology changes. It achieves this by maintaining accurate routing information in the FIB and using mechanisms like Cisco Express Forwarding-Independent Fast Convergence (CEF-IFC) to rapidly update forwarding tables