802.1X authentication
802.1X authentication involves ensuring something is what its saying it is.
Features
Supplicant - (client-end user) - Devices that are trying to connect to an 802.1X need to have software installed on them and this is known as a supplicant. The supplicant initiates the connection by activating EAP (Extensible Authentication Protocol) between the device and switch
Authenticator - A device on a network that connects a client to a network. It blocks and allows traffic. A switch is an example of an authenticator.
Authentication Server - deals with requests for access to the network. The server tells the authenticator to allow or deny the traffic. Authentication servers usually run on the RADIUS protocol.
AAA
AAA is a requirement of network security. It is a process from start to finish of network access and monitoring
Authentication: uses challenge and response methodology for granting access. This identifies users by username and password
Authorisation: After initial authentication, authorisation uses the RADIUS protocol to allow access to resources based on permission levels
Accounting: After access users can be be monitoring for billing, reporting and auditing. You can observe what users do after they have been authenticated and authorised for example when they log in and when they log out.
The next steps are to look at a practical scenario using the AAA methodology.
Topology addressing:
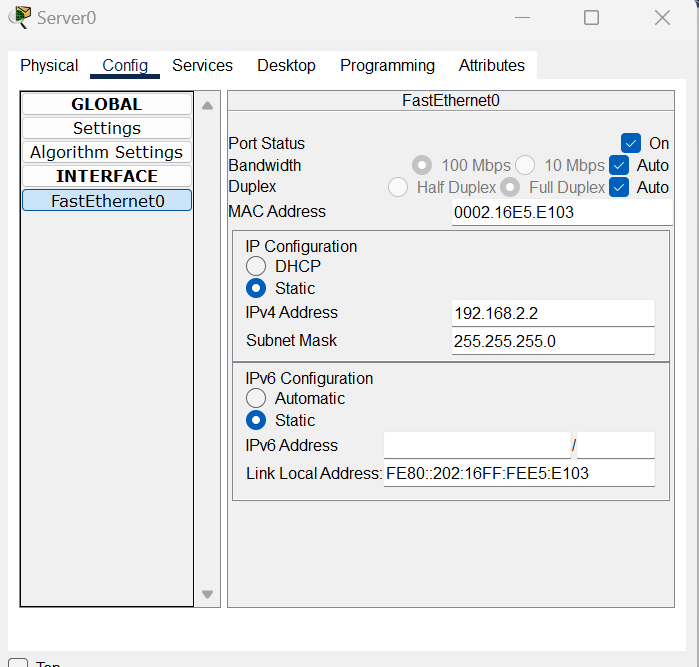
Server: 192.168.2.2
G/0/0/1: 192.168.2.1
G/0/0/0: 192.168.1.1
PC0: 192.168.1.2 (Default Gateway 192.168.1.1)
Configure IP addressing on the router:
Assign a valid IP address to your Radius Server:
Turn on AAA on the services tab, add the the router details for the network the server is on ands specify a passkey - here I have used "hello"
Configuring AAA on the router, specify the server address and the passkey you used. (note the passkey I used is not very secure so something with multiple characters, number etc may be better)
Enable remote login:
Assign an IP address for your PC:
Test the telnet connection:
Note here: To use the more secure SSH connection you would need to add the ssh configurations into the router and it is also good practice to enable passwords on your router which was discussed in previous posts.









No comments:
Post a Comment