The CIA Triad: Understanding the Fundamentals of Information Security
In the world of information security, the CIA triad is a critical concept to understand. This model provides a framework for ensuring the confidentiality, integrity, and availability (CIA) of information and is widely used in the field of information security. In this blog post, we will discuss the basics of the CIA triad, why it is important, and how it can be applied in real-world scenarios.
Confidentiality
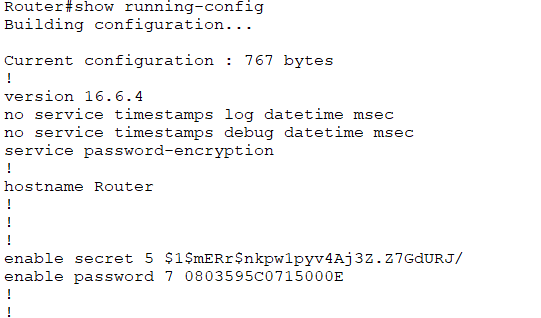
Confidentiality refers to the protection of sensitive information from unauthorized disclosure. In other words, confidentiality ensures that only authorized individuals can access sensitive information. This is achieved through the use of encryption, access control systems, and other security measures.
Integrity
Integrity refers to the accuracy and consistency of information over time. This means that information must not be altered or corrupted in any way without authorization. This is important because if information is altered or corrupted, it can lead to serious consequences such as miscommunication or misinformation. Integrity can be maintained through the use of checksums, hash functions, and digital signatures.
Availability
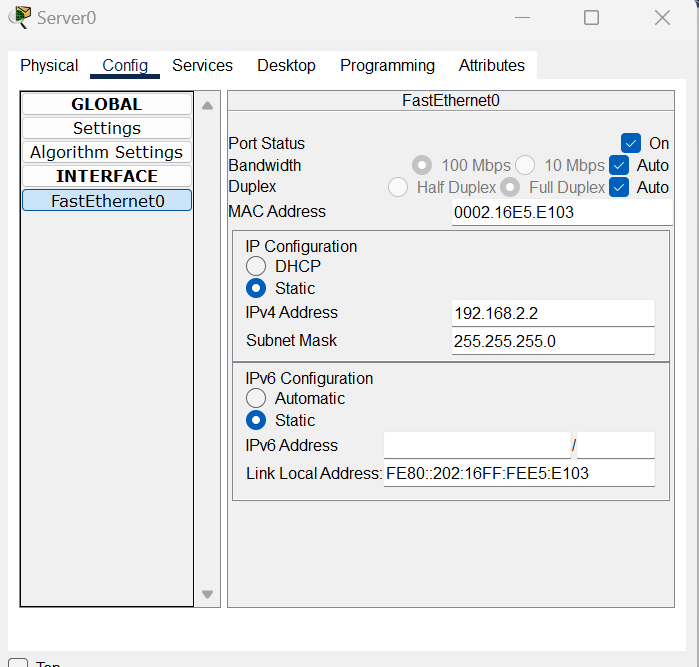
Availability refers to the ability of authorized individuals to access information when they need it. This is important because if information is not available, it can lead to significant disruption and loss of productivity. Availability is maintained through the use of backups, redundancy, and disaster recovery systems.
Why the CIA triad is important
The CIA triad is important because it provides a comprehensive framework for securing information. By focusing on confidentiality, integrity, and availability, organizations can ensure that their information is protected from unauthorized access, alteration, and loss. The CIA triad is also important because it helps organizations prioritize their security efforts, as different types of information may require different levels of protection.
How to apply the CIA triad in real-world scenarios:
The CIA triad can be applied in a variety of real-world scenarios, including:
Protecting personal information: This may include financial information, personal health information, and other sensitive data. Organizations must implement measures to ensure the confidentiality and integrity of this information, as well as ensure its availability for authorized individuals.
Securing critical infrastructure: This includes power grids, communication networks, and other systems that are critical to the functioning of society. The CIA triad can be applied to ensure that these systems are secure, reliable, and available at all times.
Protecting intellectual property: This includes confidential business information, trade secrets, and other proprietary information. Organizations must implement measures to ensure the confidentiality and integrity of this information, as well as ensure its availability to authorized individuals.
In conclusion, the CIA triad is a critical concept in the field of information security. By focusing on confidentiality, integrity, and availability, organizations can ensure the protection of their information and minimize the risk of data breaches and other security incidents. By understanding and applying the CIA triad, organizations can build a strong and effective security program that will protect their assets and reputation.