Thursday, 23 March 2023
Subnetting
Tuesday, 21 March 2023
Port security - Cisco switches
Switchport security associates specific MAC addresses of PCs with specific interfaces on a switch. It gives you the ability to restrict to a switch interface so that only authorised devices can use it. You can define the port action with three different modes : Protect(sends an alert), restrict(discards), shutdown(closes the port)
Implement Port security
Finally if we ping between the two pcs and run the show port-security interface fa0/1 command on the switch .You can now see the maximum allowed devices, port status and the mac address that has passed through.
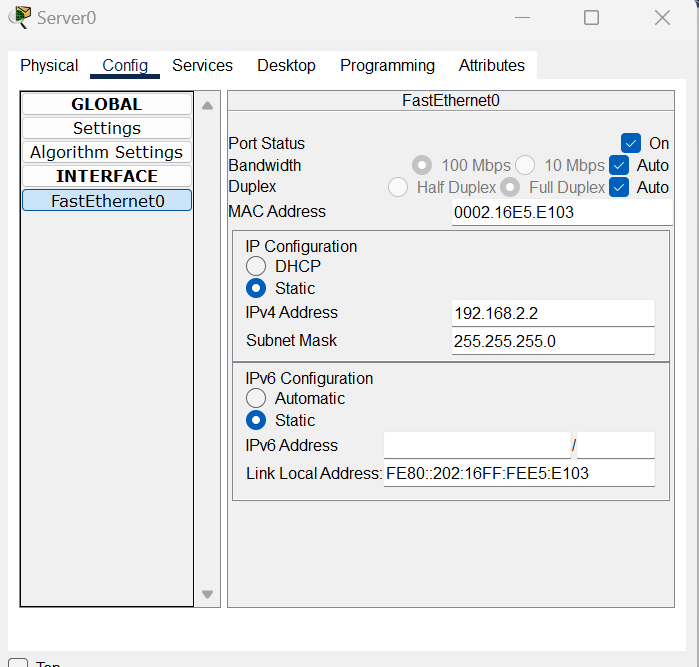
AAA - Authentication, Authorisation, Accounting
802.1X authentication
Features
AAA
Topology addressing:
Server: 192.168.2.2
G/0/0/1: 192.168.2.1
G/0/0/0: 192.168.1.1
PC0: 192.168.1.2 (Default Gateway 192.168.1.1)
Configure IP addressing on the router:
Configuring AAA on the router, specify the server address and the passkey you used. (note the passkey I used is not very secure so something with multiple characters, number etc may be better)
Enable remote login:
Assign an IP address for your PC:
Note here: To use the more secure SSH connection you would need to add the ssh configurations into the router and it is also good practice to enable passwords on your router which was discussed in previous posts.
Monday, 13 March 2023
Hyper - V - Virtualisation
What is Hyper - V?
Enabling Hyper V in Windows 11
Begin your lab journey....
Once you have Hyper V installed, embark on your lab journey. Below is a playlist for creating a replica of a domain management structure, I will keep adding to it over time...
Wednesday, 8 March 2023
Hot Standby Routing Protocol ( HSRP)
HSRP is a Cisco proprietary protocol that provides redundancy within a subnet. A virtual router is created which acts as the default gateway and a priority number is assigned to the physical routers to determine which is active and which is a standby router.
Some key concepts with HSRP;
Priority
Preempt
Hello messages
Are exchanged periodically to activate the standby router if it detects a failure on the network.
Virtual IP address
Practical activity
Technical timewasters
Below are a list of articles that made me lol...
Banking industry vs Security development
Here is a funny email exchange when the banking industry tried to influence the development of TLS - Link
MAC Address Basics
Each of a hosts network interfaces has a link layer MAC address that distinguishes it from other machines on the physical network. IP addresses are assigned to network interfaces and not machines. A mac address is made up of 48 bits or 6 bytes and is split into two parts. The first 3 bytes identify the manufacturer and the last 3 bytes are a unique serial number, so in this example the green sections are the vendor id and the black section is the interfaces unique number 32-03-C8-73-DC-A1. This is important for network engineers in spotting devices or vendors that are causing havoc on the network.
Broadcasting
Multicasting
MAC address tabling
Monday, 6 March 2023
Network Ports and Protocols Cheat Sheet
Network communications are governed by a set of rules called protocols. Each protocol is assigned a port to allow applications to communicate. Below is a list of common protocols;
| PORT NUMBER | SERVICE NAME | TRANSPORT PROTOCOL | DESCRIPTION |
| 20 | FTP-data | TCP, SCTP | File Transfer Protocol data transfer |
| 21 | FTP | TCP, UDP, SCTP | File Transfer Protocol command control |
| 22 | SSH/SCP/SFTP | TCP, UDP, SCTP | Secure Shell, secure logins, file transfers (scp,sftp), and port forwarding |
| 23 | Telnet | TCP | Telnet protocol, for unencrypted text communications |
| 25 | SMTP | TCP | Simple Mail Transfer Protocol, used for email routing between mail servers |
| 42 | WINS Replication | TCP, UDP | Microsoft Windows Internet Name Service, vulnerable to attacks on a local network |
| 43 | WHOIS | TCP, UDP | Whois service, provides domain-level information |
| 49 | TACACS | UDP; can also use TCP but not necessarily on port 49 | Terminal Access Controller Access-Control System, provides remote authentication and related services for network access |
| 53 | DNS | TCP, UDP | Domain Name System name resolver |
| 67 | DHCP/BOOTP | UDP | Dynamic Host Configuration Protocol and its predecessor Bootstrap Protocol Server; server port |
| 68 | DHCP/BOOTP | UDP | Dynamic Host Configuration Protocol and its predecessor Bootstrap Protocol Server; client port |
| 69 | TFTP | UDP | Trivial File Transfer Protocol |
| 80 | HTTP | TCP, UDP, SCTP | Hypertext Transfer Protocol (HTTP) uses TCP in versions 1.x and 2. HTTP/3 uses QUIC, a transport protocol on top of UDP |
| 88 | Kerberos | TCP, UDP | Network authentication system |
| 102 | Microsoft Exchange ISO-TSAP | TCP | Microsoft Exchange ISO Transport Service Access Point (TSAP) Class 0 protocol |
| 110 | POP3 | TCP | Post Office Protocol, version 3 (POP3) |
| 113 | Ident | TCP | Identification Protocol, for identifying the user of a particular TCP connection |
| 123 | NTP | UDP | Network Time Protocol |
| 135 | Microsoft RPC EPMAP | TCP, UDP | Microsoft Remote Procedure Call (RPC) Endpoint Mapper (EPMAP) service, for remote system access and management |
| 137 | NetBIOS-ns | TCP, UDP | NetBIOS Name Service, used for name registration and resolution |
| 138 | NetBIOS-dgm | TCP, UDP | NetBIOS Datagram Service, used for providing access to shared resources |
| 139 | NetBIOS-ssn | TCP, UDP | NetBIOS Session Service |
| 143 | IMAP | TCP, UDP | Internet Message Access Protocol (IMAP), management of electronic mail messages on a server |
| 161 | SNMP-agents (unencrypted) | UDP | Simple network management protocol; agents communicate on this port |
| 162 | SNMP-trap (unencrypted) | UDP | Simple network management protocol; listens for asynchronous traps |
| 179 | BGP | TCP | Border Gateway Protocol |
| 194 | IRC | UDP | Internet Relay Chat |
| 264 | BGMP | TCP, UDP | Border Gateway Multicast Protocol |
| 318 | TSP | TCP, UDP | Time Stamp Protocol |
| 389 | LDAP | TCP, UDP | Lightweight directory access protocol |
| 427 | SLP | TCP | Service Location Protocol |
| 443 | HTTPS (HTTP over SSL) | TCP, UDP, SCTP | Hypertext Transfer Protocol Secure (HTTPS) uses TCP in versions 1.x and 2. HTTP/3 uses QUIC, a transport protocol on top of UDP. |
| 445 | Microsoft DS SMB | TCP, UDP | Microsoft Directory Services: TCP for Active Directory, Windows shares; UDP for Server Message Block (SMB) file-sharing |
| 464 | Kerberos | TCP, UDP | For password settings on Kerberos |
| 465 | SMTP over TLS/SSL, SSM | TCP | Authenticated SMTP over TLS/SSL (SMTPS), URL Rendezvous Directory for Cisco’s Source Specific Multicast protocol (SSM) |
| 497 | Dantz Retrospect | TCP, UDP | A software suite for backing up operating systems |
| 500 | IPSec / ISAKMP / IKE | UDP | Internet Protocol Security / Internet Security Association and Key Management Protocol / Internet Key Exchange |
| 513 | rlogin | TCP | The Unix program rlogin allows users to log in on another host using a network. |
| 514 | syslog | UDP | Syslog Protocol, for collecting and organizing all of the log files sent from the various devices on a network |
| 515 | LPD/LPR | TCP | Line Printer Daemon protocol, or Line Printer Remote protocol |
| 520 | RIP | UDP | Routing Information Protocol, used to find the optimal path between source and destination networks |
| 521 | RIPng (IPv6) | UDP | Routing Information Protocol next generation, the IPv6 compatible version of RIP |
| 554 | RTSP | TCP, UDP | Real Time Streaming Protocol |
| 546 | DHCPv6 | TCP, UDP | Dynamic Host Configuration Protocol version 6. DHCPv6 Clients listen for DHCPv6 messages on UDP port 546. |
| 547 | DHCPv6 | TCP, UDP | DHCPv6 Servers and DHCPv6 Relay Agents listen for DHCPv6 messages on UDP port 547. |
| 560 | rmonitor | UDP | Remote Monitor |
| 563 | NNTP over TLS/SSL | TCP, UDP | Network News Transfer Protocol with encryption and verification |
| 587 | SMTP | TCP | For email message submission via SMTP |
| 636 | LDAP over TLS/SSL | TCP, UDP | Lightweight Directory Access Protocol over TLS/SSL |
| 639 | MSDP (PIM) | TCP | Multicast Source Discovery Protocol, which is part of the Protocol Independent Multicast (PIM) family |
| 646 | LDP (MPLS) | TCP, UDP | Label Distribution Protocol, applies to routers capable of Multiprotocol Label Switching (MPLS) |
| 691 | Microsoft Exchange | TCP | Microsoft Exchange Routing |
| 860 | iSCSI | TCP | Internet Small Computer Systems Interface |
| 873 | rsync | TCP | The rsync file synchronization protocol efficiently transfers and synchronizes files between devices and networked computers. |
| 902 | VMware Server | TCP, UDP | VMware ESXi, a hypervisor |
| 989 | FTPS | TCP | File Transfer Protocol (data) over TLS/SSL |
| 990 | FTPS | TCP | File Transfer Protocol (control) over TLS/SSL |
| 993 | IMAP over SSL (IMAPS) | TCP | Internet Message Access Protocol over TLS/SSL |
| 995 | POP3 over SSL (POP3S) | TCP, UDP | Post Office Protocol 3 over TLS/SSL |
Fast switching vs Process switching
Process Switching: Process switching is the traditional method of packet forwarding used in early routers. When a packet arrives at a router...
-
Dynamic Host Configuration Protocol (DHCP) DHCP dynamically allocates an IP address from either a pre configured router or a server. DHCP is...
-
ICMP (Internet Control Message Protocol) is a rule that network devices such as routers use to generate error messages. The Internet Control...
-
RIP (Routing Information Protocol) is an interior gateway protocol that exchanges information between routers on networks. Version 2 has see...